A Network Vulnerability Testing Program Course
A Network Vulnerability Testing Program Course is a comprehensive and strategically structured training module designed to equip learners, IT professionals, cybersecurity enthusiasts, and corporate teams with the essential knowledge, practical skills, and theoretical understanding required to identify, analyze, and mitigate potential security weaknesses across various networked systems and digital infrastructures, starting with foundational concepts such as the OSI model, network topologies, and common protocols like TCP/IP, HTTP/S, FTP, and DNS, the course gradually transitions into core elements of cybersecurity including threat modeling, vulnerability assessment frameworks like CVSS (Common Vulnerability Scoring System), and hands-on exposure to industry-standard tools such as Nmap for network scanning, Wireshark for packet analysis, Nessus and OpenVAS for vulnerability assessment, Metasploit for exploitation testing, and Burp Suite for web application penetration testing, while simultaneously introducing regulatory compliance frameworks like GDPR, HIPAA, PCI-DSS, and ISO/IEC 27001 to instill a governance perspective critical to enterprise-level risk management; learners are often taught how to set up secure testing environments using virtualization platforms like VirtualBox and VMware, where they simulate real-world attack scenarios in sandboxed labs featuring deliberately vulnerable systems such as DVWA (Damn Vulnerable Web App), OWASP Juice Shop, and Metasploitable, allowing them to experiment with enumeration, reconnaissance, and privilege escalation techniques in a legally and ethically controlled space, and they also gain insight into scripting automated scans using Python or Bash for repetitive tasks, as well as leveraging APIs provided by scanning tools for integration with CI/CD pipelines to support DevSecOps practices, all while fostering a mindset oriented toward continuous learning, responsible disclosure, and proactive threat hunting; the course usually delves into vulnerability management lifecycle stages such as identification, evaluation, prioritization, remediation, and reporting, emphasizing documentation and communication skills through real-world case studies where learners write detailed vulnerability reports with executive summaries and technical appendices, analyze past data breaches like Equifax or SolarWinds to understand how vulnerabilities were exploited, and participate in Capture the Flag (CTF) competitions or red team/blue team simulations to build teamwork and offensive/defensive skills; instructors often supplement training with interactive modules, live demonstrations, quizzes, and assignments, and some courses include certifications or prepare students for credentials like CompTIA Security+, CEH (Certified Ethical Hacker), OSCP (Offensive Security Certified Professional), or GIAC certifications that validate professional capabilities and open doors to roles such as penetration tester, security analyst, vulnerability researcher, or network security engineer; learners are encouraged to contribute to open-source security projects, maintain a GitHub portfolio, engage in responsible vulnerability disclosure programs, and remain updated with advisories from CVE databases, NIST NVD, and community platforms like Exploit-DB or HackerOne; ultimately, the course not only empowers individuals to identify technical flaws in systems but also emphasizes the strategic importance of integrating vulnerability testing into broader organizational security postures through risk assessments, security policies, and incident response planning, ensuring that network vulnerability testing becomes not a one-time event but a continuous process embedded in an organization’s security lifecycle, with the final objective of fostering a culture of cyber resilience, proactive defense, and ethical responsibility in the ever-evolving threat landscape of digital communication and commerce.
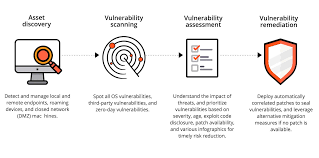
Networking and Cybersecurity Fundamentals
Before diving into vulnerability testing, students must grasp the essential concepts of computer networking and cybersecurity. These include the OSI and TCP/IP models, the roles of routers, switches, and firewalls, common protocols like HTTP, HTTPS, DNS, FTP, and SMTP, and the architecture of local and wide-area networks. Understanding how data flows within and across networks is key to identifying possible attack surfaces. Learners also explore concepts such as IP addressing, subnetting, MAC addresses, and VLANs. Cybersecurity fundamentals covered include the CIA triad (Confidentiality, Integrity, Availability), threat actors, types of attacks (DoS, MITM, phishing, malware), and the basics of risk assessment and threat modeling. This foundational knowledge enables learners to understand how attackers exploit weak network configurations or unpatched services and helps them lay the groundwork for designing secure infrastructures.
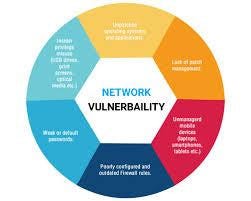
Vulnerability Types and Threat Landscape
The course then introduces students to the types of vulnerabilities that typically affect networks and systems. These include misconfigurations, unpatched software, weak or default passwords, open ports, outdated protocols, and exposed services. The curriculum examines how these vulnerabilities can be exploited in real-world scenarios, often referencing past incidents such as the Equifax breach (due to an unpatched Apache Struts vulnerability) or the WannaCry ransomware attack (exploiting the SMBv1 protocol). Students also learn about software and hardware vulnerabilities, the concept of zero-day flaws, and emerging threats related to IoT, mobile networks, and cloud services. A strong emphasis is placed on maintaining situational awareness of the current cyber threat landscape by following feeds from CVE databases, MITRE ATT&CK, and NIST’s National Vulnerability Database (NVD).
Vulnerability Assessment Tools and Techniques
An essential component of the course involves learning to use vulnerability assessment tools. Students are taught how to conduct reconnaissance using tools like Nmap and Zenmap, gather intelligence through passive and active scanning, identify open ports and running services, and analyze operating systems and software versions for known vulnerabilities. Tools like Nessus, OpenVAS, and Qualys are introduced for comprehensive vulnerability scanning, and learners practice configuring scan policies, interpreting risk ratings, and generating reports. They also gain experience using Nikto for web server scanning, Burp Suite for web application security testing, and Wireshark for network traffic analysis. Advanced modules may explore the Metasploit Framework to validate vulnerabilities through controlled exploitation, teaching the importance of confirming findings while minimizing impact on production systems.
Setting Up Safe Testing Environments
Network vulnerability testing must be done in a secure and legal environment. The course guides students in setting up virtual labs using platforms like VirtualBox or VMware, along with virtual networks that simulate enterprise environments. Popular intentionally vulnerable systems such as DVWA (Damn Vulnerable Web App), Metasploitable, and OWASP Juice Shop are used for hands-on practice. Students learn the principles of network segmentation, isolation, and sandboxing to ensure tests do not inadvertently affect live systems. These safe environments are crucial for ethical hacking, red teaming exercises, and vulnerability validation, allowing learners to explore real-world scenarios without legal risks.
Manual vs Automated Testing
Both manual and automated testing approaches are explored to give students a well-rounded perspective. Automated tools like Nessus and Qualys help discover a large number of known vulnerabilities quickly, but learners are also taught the value of manual inspection to identify logic flaws, misconfigurations, or business logic vulnerabilities that tools may miss. Techniques like banner grabbing, OS fingerprinting, service enumeration, and manual testing of SSL/TLS configurations are demonstrated. Students also learn to craft custom scripts using Python, Bash, or PowerShell to automate repetitive tasks or customize scans, giving them greater control and flexibility during assessments.
Comments on “Network Vulnerability Testing Program Course”