In the digital age, where nearly every individual and business relies on mobile apps and web platforms, cybersecurity becomes mission-critical. Pentesting — or penetration testing — is the art and science of probing these systems for weaknesses before malicious actors exploit them. At CyberYaan, we hold that knowledge is the greatest defense. This deep-dive examines both web and mobile app pentesting methodologies, tools, and best practices. Whether you’re a budding security analyst or an IT manager, this guide equips you with expertise to fortify your digital infrastructure.
CyberYaan’s Complete Guide to Mobile and Web Pentesting
In today’s hyper-connected digital landscape, every application you interact with — be it a mobile app for banking or a website for e-commerce — is a potential target for cyber threats. This reality makes penetration testing (commonly referred to as pentesting) a crucial part of cybersecurity strategies adopted by organizations. At CyberYaan, we believe cybersecurity is not just a technical protocol but a culture of resilience. This blog aims to explore the depths of mobile and web application penetration testing, focusing on methodologies, challenges, tools, and CyberYaan’s contributions in building a secure cyber ecosystem. Whether you’re a developer, ethical hacker, IT auditor, or security enthusiast, understanding the fundamentals and advanced layers of mobile and web pentesting is essential for protecting digital assets.
Penetration testing is a simulated cyberattack performed to evaluate the security posture of a system. It involves the use of manual and automated techniques to identify vulnerabilities that could be exploited by malicious users. In mobile and web environments, pentesting becomes particularly critical because these platforms process sensitive user data and often serve as the frontline interfaces of businesses. CyberYaan approaches penetration testing not just as a one-time audit, but as an ongoing strategy embedded into the application development lifecycle. This blog sheds light on the entire process — from reconnaissance to reporting — offering you a complete toolkit to understand and execute mobile and web penetration testing.
Web application penetration testing starts with reconnaissance, the phase where a pentester collects as much information as possible about the target system. This phase can be passive — like gathering publicly available data from search engines, social media, or public code repositories — or active, which involves network scanning, DNS interrogation, and directory brute-forcing. Tools like Nmap, DirBuster, Sublist3r, and Burp Suite’s spider feature come in handy at this stage. Recon helps in mapping out the application’s architecture, identifying exposed endpoints, and setting the stage for deeper analysis. It’s essentially the blueprint of your target and forms the foundation of all further testing.
Following reconnaissance, pentesters dive into vulnerability analysis. This phase includes testing for the most common and dangerous web vulnerabilities outlined by the OWASP Top 10, such as injection flaws, broken access control, cross-site scripting (XSS), and security misconfigurations. Each vulnerability has its own set of exploit techniques and requires a combination of automated tools and manual logic to uncover. For example, SQLMap can be used to identify SQL injection flaws, while Burp Suite can detect broken session management or input validation gaps. CyberYaan’s pentesters often create customized payloads to bypass WAFs and detect hidden flaws that generic scanners might miss.
One of the crucial elements of web pentesting is session management and authentication testing. These are core components of any secure application, and flaws in them can result in account takeovers, privilege escalations, and impersonation attacks. Pentesters examine cookies, tokens, login flows, and multifactor authentication mechanisms to ensure they can’t be bypassed or hijacked. Techniques include brute-forcing login credentials, replaying tokens, or intercepting session cookies. CyberYaan utilizes tools like Burp Suite Intruder, Hydra, and JWT decoder plugins to test the robustness of authentication mechanisms.
Equally important is testing the business logic of an application. Unlike technical vulnerabilities, business logic flaws arise from poor design or incorrect assumptions about how users interact with the system. These can include bypassing payment flows, exploiting referral bonuses, or misusing rate limits to gain unfair advantages. Since automated scanners often miss these flaws, manual exploration and creative test cases are vital. At CyberYaan, we encourage our pentesters to “think like a user, break like a hacker” when probing for logical flaws. It’s about identifying how an attacker could abuse legitimate features for malicious gains.
After vulnerabilities are identified and exploited in a controlled manner, pentesters proceed to the reporting phase. This isn’t merely about listing issues but presenting them in a structured, risk-based format. Each vulnerability must include a clear title, technical description, potential impact, steps to reproduce, screenshots or logs as evidence, and actionable recommendations. CyberYaan’s reports include an executive summary tailored for management and a detailed technical section for developers and IT staff. Effective reporting bridges the gap between discovery and remediation, ensuring vulnerabilities are not just identified but also fixed appropriately.
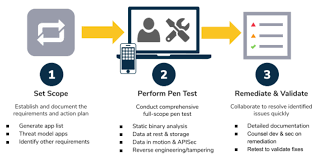
Switching to mobile application penetration testing, the methodology may seem similar on the surface but carries a different set of challenges. Mobile applications are typically platform-specific, running on Android or iOS, each with its own security architecture. Mobile apps also store sensitive data on local devices, which may be vulnerable to tampering or extraction. Additionally, they often communicate with backend APIs that may be less secure than the mobile frontend. CyberYaan’s mobile pentesting framework is designed to cover all these layers — static analysis, dynamic analysis, and backend API testing — ensuring comprehensive coverage.
Static analysis is the first step in mobile pentesting. It involves decompiling the application binary (copyright for Android or IPA for iOS) and examining the source code, configuration files, and embedded resources. Tools like JADX, MobSF, APKTool, and Frida help in decompiling the code and inspecting it for hardcoded credentials, API keys, insecure permissions, or weak encryption algorithms. For instance, if an Android app stores sensitive user tokens in SharedPreferences without encryption, that becomes a major red flag. Similarly, in iOS apps, misuse of Keychain or insecure local databases could expose confidential data to attackers.
Dynamic analysis focuses on monitoring the app’s behavior during runtime. This includes capturing traffic, analyzing API interactions, testing user roles, and injecting malicious payloads. Intercepting mobile traffic typically requires setting up a proxy like Burp Suite or mitmproxy and installing a custom certificate on the mobile device to perform SSL inspection. However, many modern apps implement SSL pinning, which blocks proxy interception. Tools like Frida or Objection allow pentesters to bypass SSL pinning dynamically, giving them full visibility into app-server communications. This is where many hidden vulnerabilities — like insufficient authentication on API endpoints or improper input validation — can be uncovered.
Another critical area in mobile testing is local storage and inter-app communication. Mobile apps often store cache files, logs, session information, and even cryptographic keys on the device. If these aren’t properly protected using encrypted storage or Android’s Keystore/iOS Keychain, attackers with physical access or root permissions can extract this data. Moreover, insecure implementation of Android intents or iOS URL schemes can allow unauthorized apps to invoke or hijack app functionality. At CyberYaan, we simulate such attacks using test apps and virtual devices to replicate real-world exploitation scenarios and identify these flaws in advance.
Mobile applications also rely heavily on third-party libraries and SDKs, some of which may have their own vulnerabilities. During a pentest, it’s important to identify these dependencies and check for outdated or vulnerable versions. Tools like MobSF and dependency scanners can help flag known CVEs. Additionally, apps that load code dynamically or rely on external sources (like plugins or mini-apps) introduce a larger attack surface. CyberYaan’s testing methodology includes validating the integrity and trustworthiness of external resources to ensure the app doesn’t unknowingly execute malicious content.
Both in web and mobile pentesting, the backend APIs play a central role. Many apps are nothing but frontends that communicate with powerful backend servers handling user data, payment processing, and business logic. These APIs need to be tested thoroughly for authentication issues, authorization checks, input sanitization, and data leakage. Techniques like token manipulation, fuzzing API parameters, chaining endpoints, and using out-of-bound requests are common. CyberYaan uses Postman and Burp Suite to craft and send custom API requests that mimic real attacks. Identifying improper access controls or overly permissive CORS policies is a regular occurrence.
Beyond technical testing, CyberYaan also focuses on integrating pentesting into the development lifecycle. This is done through shift-left practices, DevSecOps principles, and secure coding training for development teams. We believe that pentesting should not be a one-time compliance requirement but a continuous process. Automated scanners can be integrated into CI/CD pipelines to catch common issues early, while periodic manual pentests can catch complex logic or integration flaws. CyberYaan’s advisory team also works with organizations to develop custom secure development policies and code review guidelines.
Another essential part of our pentesting philosophy is continuous learning and community engagement. Cybersecurity is an ever-evolving field, and staying updated is vital. CyberYaan actively participates in bug bounty platforms, capture-the-flag events, and open-source security tool development. We encourage aspiring pentesters to contribute to platforms like HackerOne, Bugcrowd, and OWASP, and to learn from shared experiences. Real-world testing teaches more than theoretical reading, and hands-on exposure is key to becoming a skilled pentester. Our CyberYaan Academy offers structured training paths in mobile and web pentesting, with labs, certification support, and mentorship.
To illustrate the impact of effective pentesting, let’s consider a few real-world case studies handled by CyberYaan. In one instance, a fintech mobile app was storing session tokens in clear text inside Android logs. Upon rooting the device and accessing the logs, we were able to hijack a session and perform unauthorized fund transfers. After our report, the development team adopted secure logging practices and encrypted token storage. In another case, an e-commerce web app failed to invalidate user sessions after logout. This led to a situation where an attacker with an old session cookie could still access the victim’s account. CyberYaan’s report led to the implementation of proper session termination and IP-based session validation.
Reporting is the final, but arguably most important, phase of a penetration test. A well-documented report not only describes what went wrong but educates stakeholders on how to fix it. At CyberYaan, we categorize each finding by severity — Critical, High, Medium, Low — and offer customized remediation plans. We also conduct retesting once fixes are implemented, ensuring closure of the vulnerability loop. Our reports are designed to support audits, compliance checks, and internal risk management processes, providing long-term value beyond just technical details.
In conclusion, mobile and web penetration testing are critical components of any organization’s cybersecurity framework. While tools and techniques may differ, the core philosophy remains the same: identify vulnerabilities before attackers do, understand the risks, and fix them proactively. With mobile apps becoming the gateway to personal and financial data, and web applications being the backbone of global commerce, secure coding and regular pentesting have never been more important. CyberYaan’s mission is to empower individuals and enterprises with the skills, tools, and mindset to stay ahead in this cybersecurity arms race. From in-depth pentests to workshops and community programs, we strive to build a safer digital world — one test at a time.
Another often-overlooked factor in web and mobile pentesting is misconfigured security headers. HTTP headers such as are vital for browser-based defenses. Improper configuration of these headers can expose web applications to clickjacking, MIME-type confusion, and script injection attacks. At CyberYaan, we systematically analyze header responses using automated scripts and browser developer tools, ensuring these protective measures are correctly deployed and enforced. This seemingly minor detail can significantly reduce an application's attack surface.
Furthermore, Cross-Origin Resource Sharing (CORS) is another critical web security concern that often goes unnoticed. If CORS policies are too permissive — allowing * origins or enabling credentials without proper validation—it could allow unauthorized sites to interact with authenticated sessions. This could be exploited to steal data or perform unauthorized actions. During a pentest, CyberYaan tests for insecure CORS configurations by crafting malicious domains and checking for data access across origins. This is a classic example of how a server-side misconfiguration can create serious client-side vulnerabilities.
Third-party integrations also introduce a range of vulnerabilities in both mobile and web applications. Whether it’s a payment gateway, analytics SDK, or social login provider, each integration point adds a potential weakness. Attackers often exploit these integrations by tampering with callback URLs, injecting JavaScript payloads, or abusing webhook endpoints. CyberYaan’s pentesting process includes verifying the security of these external interactions, ensuring input/output sanitization and signature verification mechanisms are in place. We often see that even when core application code is secure, weaknesses exist in how external services are consumed.
In the context of mobile applications, root and jailbreak detection is an important but sometimes bypassable feature. Many developers implement basic checks to prevent rooted devices from running their apps. However, these checks can often be bypassed using tools like Magisk, Xposed, or Frida scripts. At CyberYaan, we perform tests on both emulated and rooted/jailbroken environments to validate the robustness of such security controls. We also test for anti-debugging techniques and code obfuscation measures to ensure they can’t be easily reverse-engineered by malicious actors.
When it comes to cryptography, improper implementation can be just as dangerous as having no encryption at all. Many developers mistakenly use hardcoded keys, outdated algorithms like MD5 or SHA1, or insecure modes like ECB for block ciphers. In mobile apps, cryptographic misuse is commonly detected during static analysis, while web apps can leak information through poorly implemented HTTPS or flawed JWT configurations. CyberYaan’s pentesting checklist includes inspecting encryption libraries, key management practices, and ensuring that modern standards like AES-GCM and SHA-256 are being applied correctly with proper key rotation.
Another emerging area of concern is client-side security in single-page applications (SPAs). With frameworks like React, Angular, and Vue powering modern web apps, logic and data flow are increasingly handled on the client side. This raises the risk of client-side vulnerabilities such as DOM-based XSS, local storage token theft, and state manipulation. CyberYaan uses browser-based instrumentation and DOM inspection tools to identify potential flaws in frontend logic. We look for insecure JavaScript APIs, exposed routes, and poorly implemented client-side access controls — especially in apps that rely on front-end role verification instead of server-side enforcement.
In mobile applications, insecure APIs are a persistent threat. Mobile apps often rely heavily on backend APIs to perform all major functions — from authentication to transactions. However, if these APIs are not properly secured, attackers can reverse-engineer the app, extract API endpoints, and abuse them from external tools. At CyberYaan, we often simulate this by extracting endpoints from the decompiled source or capturing traffic, and then using Postman or custom scripts to replay requests. We test for broken authentication, missing rate limits, parameter tampering, and unrestricted resource access.
Another growing threat in both mobile and web applications is insufficient logging and monitoring. In a world where cyber breaches are becoming more frequent, being able to detect and respond to suspicious activity quickly is crucial. Unfortunately, many apps either do not log significant security events or log them improperly. CyberYaan evaluates logging mechanisms to ensure that failed login attempts, access violations, and data exfiltration attempts are recorded and alertable. We also ensure sensitive data — like passwords or tokens — is not inadvertently logged in plaintext, which could pose privacy risks.
Post-exploitation analysis is an advanced phase of penetration testing where the attacker simulates actions after gaining access to the system. This could include lateral movement, privilege escalation, data exfiltration, or persistence mechanisms. In a mobile app context, this might mean exploiting local databases to uncover stored credentials. In web applications, it could involve chaining multiple vulnerabilities to escalate access from a low-privileged user to an admin. CyberYaan’s senior pentesters perform such chaining scenarios to demonstrate real-world risk and guide organizations in prioritizing their patching efforts.
Social engineering simulations are sometimes bundled into pentesting engagements to test the human layer of security. While technically outside the scope of pure application pentesting, phishing simulations, credential harvesting, and fake app deployments can reveal shocking vulnerabilities in user behavior and organizational policy. CyberYaan occasionally includes social engineering components, especially when working with high-risk industries like finance, healthcare, or education, where phishing and malicious apps are common attack vectors.
In recent years, the integration of DevSecOps pipelines has transformed how security testing is performed. Instead of being a late-stage, manual process, pentesting is now being incorporated into the CI/CD workflow using tools like SonarQube, GitHub Actions, and GitLab Security. Static Application Security Testing (SAST), Dynamic Application Security Testing (DAST), and Software Composition Analysis (SCA) tools are increasingly used to automate parts of the testing process. While this automation is valuable, it cannot replace the critical thinking and creative exploitation strategies of manual pentesting. CyberYaan believes in blending automation with expert insight to deliver meaningful results.
The role of compliance and regulatory standards in shaping the need for mobile and web pentesting cannot be understated. Frameworks like GDPR, HIPAA, PCI-DSS, and ISO 27001 either recommend or mandate periodic penetration testing as part of risk management and data protection strategies. CyberYaan helps organizations align their pentesting efforts with these regulations, offering tailored reports and compliance checklists to ensure audit-readiness. Our pentesting approach not only highlights risks but also maps findings directly to relevant compliance controls, simplifying remediation and reporting.
Finally, education and awareness remain the most powerful tools in the fight against cyber threats. CyberYaan continuously invests in training programs, webinars, CTFs (capture the flag challenges), and hands-on labs to educate both technical and non-technical stakeholders. Developers are trained in secure coding, product managers learn secure design principles, and end-users are taught how to identify malicious behavior in mobile and web environments. Knowledge transfer is a critical step in converting pentesting from a reactive to a proactive security discipline.
To summarize, mobile and web application penetration testing is no longer a luxury — it is a necessity. With the increasing complexity of digital systems, growing cyber threats, and tightening compliance requirements, organizations must adopt a holistic approach to securing their applications. Web pentesting addresses threats to publicly exposed digital assets, while mobile pentesting protects the data on your users’ devices and ensures secure backend communication. The key lies in combining automation with manual expertise, proactive strategy with reactive validation, and continuous learning with systematic execution. CyberYaan stands at the forefront of this mission — helping enterprises build trust, protect data, and stay ahead in a world where security threats evolve faster than ever.
As digital transformation continues to accelerate, your applications will reach more users, more devices, and more geographies. This growth must be matched with equal focus on robust, repeatable, and responsive security testing. Through this in-depth blog, we’ve outlined not just the process, but the mindset of mobile and web pentesting — a mindset rooted in curiosity, responsibility, and precision. Let this be your call to action. Audit your systems, test your defenses, and build secure applications from the ground up. Because when you partner with CyberYaan, security isn’t just a feature — it’s a foundation.
The ever-growing diversity of device ecosystems also impacts how mobile and web pentests are conducted. With users accessing services via smartphones, tablets, desktops, smart TVs, and even wearable devices, the attack surface has expanded dramatically. Each platform has unique security limitations and configurations — an app working flawlessly on a flagship Android phone may behave differently on a low-end device running an outdated OS. Similarly, web apps may face rendering issues, session handling bugs, or CORS misconfigurations on alternate browsers. At CyberYaan, we ensure that tests are performed across a variety of devices and browsers to simulate real-world environments as closely as possible. This ensures a more accurate risk picture for organizations aiming for global user bases.
In addition to multi-device testing, network environment testing plays a crucial role in realistic pentesting. Applications behave differently over Wi-Fi, mobile data, VPNs, or restricted enterprise networks. These differences can affect how apps validate SSL certificates, maintain session integrity, or handle data caching. For example, some applications bypass encryption on cellular networks or misconfigure data usage warnings, exposing critical data. CyberYaan incorporates network simulation environments during mobile pentesting to evaluate whether applications remain secure even in compromised or low-trust networks — particularly important for apps used in remote or public settings.
An advanced concept gaining traction in mobile security is runtime instrumentation, which allows pentesters to manipulate application behavior during execution. This is especially useful when attempting to bypass client-side validations or observe encrypted data handling in real time. Tools like Frida, Xposed, and Cycript can inject scripts into the running app to alter logic or capture values mid-execution. For instance, a pentester can use Frida to override a login success condition, effectively bypassing authentication. CyberYaan’s mobile pentesters routinely use runtime instrumentation techniques to test for insecure implementations of core functions such as password validators, biometric checks, and transaction limits.
Cloud-hosted web applications introduce another layer of complexity in pentesting engagements. Today, most web backends are hosted on platforms like AWS, Azure, or Google Cloud, making them part of a shared responsibility model. While the cloud provider secures the infrastructure, the application owner is responsible for securing their configuration and code. Common mistakes include exposing unsecured S3 buckets, leaving default keys in environment variables, or misconfiguring IAM roles. CyberYaan’s pentesters conduct cloud-aware web application testing that includes analyzing cloud storage, serverless functions (like AWS Lambda), and CI/CD pipelines for vulnerabilities, offering a broader and deeper security insight.
One particularly challenging aspect of mobile pentesting is reverse engineering proprietary protocols used for device-to-app communication, especially in IoT contexts. Many apps communicate with hardware via Bluetooth, NFC, or proprietary APIs, bypassing traditional HTTP-based traffic. This presents an opaque attack surface unless the pentester can decode and analyze the communication protocol. CyberYaan’s mobile team often uses packet sniffers like Wireshark, BLE sniffer tools, and hardware debuggers to understand how mobile apps interact with external devices — essential in industries such as healthcare, automotive, and smart homes.
In web applications, a frequent oversight is the improper use of third-party JavaScript libraries. Many sites load JavaScript code from CDNs, ad networks, or analytics providers. If these external scripts are compromised or replaced, they can serve as a conduit for malware or data theft. This issue, known as JavaScript dependency hijacking, was exploited in several high-profile supply chain attacks. At CyberYaan, we audit web applications for script integrity, enforcing Subresource Integrity (SRI) where necessary, and alert developers about risky third-party inclusions that may impact data privacy and site integrity.
With the rise of Progressive Web Apps (PWAs) and hybrid mobile applications built on frameworks like React Native or Flutter, the line between web and mobile security testing is blurring. These applications often use shared codebases and rely on the same RESTful APIs and cloud infrastructure. However, they also introduce new vectors such as insecure service workers, misconfigured web manifests, and improperly sandboxed local storage. CyberYaan’s hybrid app pentesting framework bridges the gap by combining techniques from both mobile and web paradigms, ensuring full-stack coverage across platforms.
Ethical considerations are central to every pentesting engagement CyberYaan undertakes. While the goal is to simulate real-world attacks, our approach is governed by strict legal and ethical boundaries. Every test is conducted under signed authorization, and we ensure that no production data is altered, corrupted, or exposed during the process. Our pentesters follow industry standards such as the OWASP Testing Guide, NIST SP 800–115, and PTES (Penetration Testing Execution Standard). Ethics are especially important when testing sensitive applications in healthcare, education, or financial sectors, where even a small misstep can have serious regulatory consequences.
Looking forward, the landscape of mobile and web pentesting is poised to evolve rapidly. Technologies like AI and machine learning, while offering advanced detection and response capabilities, also introduce novel attack surfaces. Adversarial machine learning, model poisoning, and prompt injection attacks on AI-driven apps are becoming more common. At CyberYaan, we’re actively researching these emerging threats, developing new testing methodologies for AI-integrated applications and conversational interfaces like chatbots, voice assistants, and generative APIs.
Another area of interest is zero trust architecture, where every user, device, and application is continuously verified, regardless of location. This paradigm shifts the focus from perimeter-based defenses to identity-based security, forcing pentesters to simulate insider threats and privilege escalations more rigorously. CyberYaan is increasingly called upon to conduct red team simulations within zero-trust environments, helping organizations test their detection, response, and micro-segmentation controls against sophisticated internal attacks.
The integration of blockchain technology into apps also creates unique challenges for pentesters. Smart contracts, tokenized services, and decentralized applications (copyright) require specialized testing methods. Bugs in smart contracts — such as reentrancy, gas limit overflow, or timestamp manipulation — can have irreversible financial consequences. CyberYaan is expanding its capabilities to offer Web3 and smart contract audits, employing tools like Mythril, Slither, and Tenderly, alongside manual code reviews and simulated chain forking to assess risk in decentralized ecosystems.
At CyberYaan, we view every penetration test not just as a checklist-driven service, but as a collaborative engagement aimed at improving digital trust. Our mission is rooted in the idea that cybersecurity should be proactive, not reactive. We invest in community-driven research, contribute to open-source tooling, and mentor the next generation of ethical hackers through CyberYaan Academy. Every successful pentest is an opportunity to learn, share, and strengthen the wider digital ecosystem. Whether it’s uncovering a critical zero-day or helping a startup build secure APIs from day one, our commitment remains the same: securing the future, one line of code at a time.
Comments on “CyberYaan’s Comprehensive Guide to Mobile & Web Pentesting: Strategies, Tools & Best Practice”